Four Quick Questions and Answers About Ransomware and Bitcoin
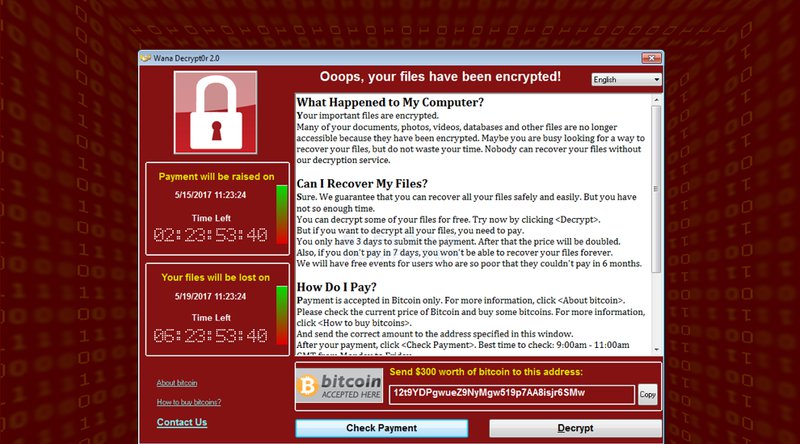
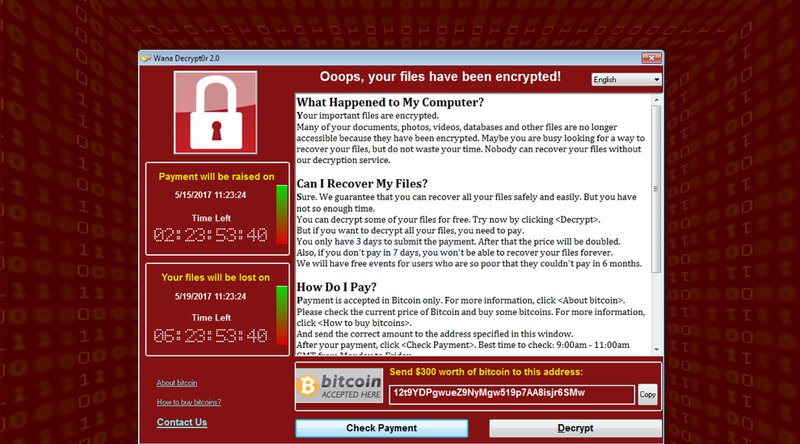
Bitcoin got caught in another media storm this week, though only in a supporting role this time around. The ongoing ransomware attack by the name of “WannaCry,” sometimes also referred to as “WannaCrypt0r,” “Wcry,” “WanaCry,” “WannaCrypt” or “Wana Decrypt0r,” infected over 230,000 computers in over 150 countries over the past couple of days, and demands that victims pay a ransom in the cryptocurrency.
So what is ransomware, and what does Bitcoin have to do with all of this?
What Is Ransomware?
Ransomware is a type of computer virus that encrypts data with a secret key. Only if a payment is made, typically in bitcoin, is the decryption key provided so victims can regain access to their data — or at least that’s the promise. An infected computer is quite literally held ransom, for actual money: bitcoin.
Unfortunately, ransomware is quickly growing in scope, and fast turning into a booming business for cybercriminals. In 2015, some estimated $24 million was paid to unlock computers, according to the FBI; in 2016, it hit a dazzling $1 billion. And that’s only expected to get worse this year.
WannaCry, which started last Friday, is the biggest ransomware attack the world has seen so far. This is mostly because WannaCry is not only ransomware, but also a “worm.” This worm uses an exploit developed by the NSA that abuses a weakness in older Windows PCs, which lets it forward itself to more and more computers: over 230,000 of them at the time of writing.
WannaCry also affected several notable targets over the past week, including Spanish phone provider Telefónica, parts of Britain’s National Health Service (NHS), U.S. delivery service FedEx, German railways Deutsche Bahn, LATAM Airlines and more.
How Successful Is Ransomware?
Ransomware attacks seem to be relatively successful in general. According to research by cybersecurity firm Trustlook, for example, over one in three victims of ransomware pay up. And a survey by IBM even showed that 70 percent of businesses infected with ransomware paid the ransom.
WannaCry, however, has not been nearly as successful — or at least not yet. At the time of writing, some 40 bitcoins have been paid to the three Bitcoin addresses associated with WannaCry. At an exchange rate of $1,700, that adds up to about $68,000 in total gains for the attackers. This is perhaps a significant amount in itself, but still modest when taking into account that well over 200,000 computers have been affected, and the ransom demanded is between $300 and $600.
The damage has probably been contained, to a large extent, because it didn’t take long for a security researcher who blogs as “MalwareTech” to find an effective kill switch. He simply registered a website that was mentioned in the code of WannaCry, which disabled at least the initial version of the ransomware.
Additionally, WannaCry gave its victims a week to pay up — though the price to unlock the encrypted data does double from $300 to $600 after four days. Given that a week hasn’t passed since the first reports of infections, it’s possible there will be another surge of payments over the next week.
Why Does Ransomware Use Bitcoin?
Ransomware does not technically require bitcoin. Indeed, there are known cases of ransomware that existed decades before Bitcoin was even invented.
However, bitcoin (and similar cryptocurrencies) can make ransomware much more effective. This is mostly because Bitcoin transactions are instant, reliable, relatively anonymous, easy to verify, and irreversible. Additionally, Bitcoin payments can potentially be made programmable, so a payment automatically sends a decryption key to a victim once a payment is made — though WannaCry did not utilize this possibility.
At the same time, however, the Bitcoin blockchain is also completely transparent. This is why it’s possible to trace exactly how much has been paid to WannaCry. It also means that it may not be very easy for the attackers to convert their bitcoins into fiat currency, or even spend them. If they ever do try to move the funds without taking appropriate precautions, they could get caught. Instead they’ll have to first mix and scramble their coins, which is possible but not necessarily easy to do.
What Can You Do About Ransomware?
The main source of the ransomware problem is not so much Bitcoin, it’s insecure computers. The fact that any malware can nest itself into computers is a problem in itself. Even without ransomware, it means that files can be stolen, edited or otherwise corrupted.
The solution, therefore, is as simple as it is boring: make sure your operating system is up to date and secure. WannaCry in particular was able to affect so many computers because they were running older versions of Windows. Upgraded computers are no longer vulnerable.
Additionally, you want to make sure to never click suspicious links in emails you receive. WannaCry initially spread itself through such links.
Furthermore, you should make sure to back up your data regularly. If you have your data backed up, you should be able to simply update your computer and restore your files without having to pay anything.
And last but not least, it is not recommended that you pay the ransom. For one, you never know for sure that paying up will actually solve your problem; the attacker could simply lie or perhaps even encrypt your data again. And two, as more people pay the ransom, this trend is more likely to grow.
Though, of course, this is easier said than done. Choosing to not make a ransom payment may not be a viable option if your most valuable files are inaccessible and you don’t have them safely backed up elsewhere …
The post Four Quick Questions and Answers About Ransomware and Bitcoin appeared first on Bitcoin Magazine.